This article will tell you about Cryptography, Cryptographic methods, and the Pros, Cons of Cryptographic methods.
What are Cryptographic Methods
To understand what cryptographic methods are and how they work, we need first to understand the origin of cryptography. Cryptography is a popular term these days. You will hear it mentioned in the news, read it in newspapers, or hear it frequently used by those with technical IT know-how. It is derived from the Greek word Kryptos which means concealed or hidden. Cryptography is the science that deals with the techniques and methods of concealing messages and their meaning to make them immune to vicious attacks by establishing a safe communication platform free from eavesdroppers and prying eyes.
How Does Cryptography Work To Secure Data
Have you ever wondered why there are so many digital certificates providers these days? The reason is that there are so many cybersecurity attacks these days, and the digital certificate providers are in to provide SSL certificates that try to minimize the cases of cyber attacks. The likes of Symantec, GoDaddy, GeoTrust, and Comodo (the makers and creators of Comodo positive SSL Wildcard), are all in the business of trying to make the internet a secure haven. Their certificates apply the cryptographic methods in securing the internet, which brings us to how cryptography works to secure data and digital resources.
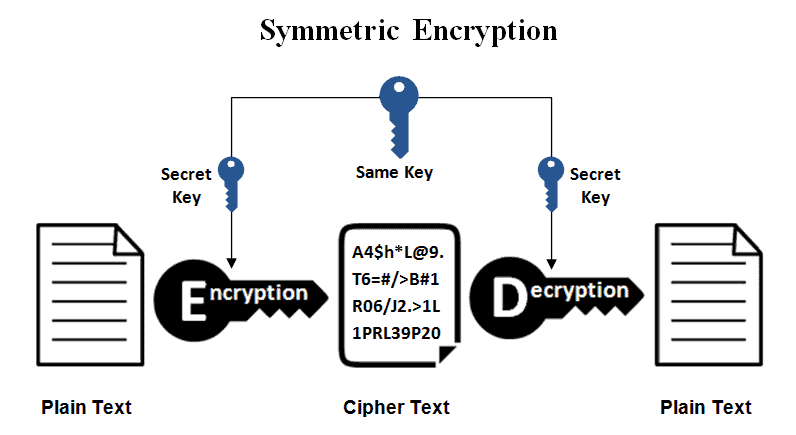
Cryptography works simply by converting cleartext (also called plaintext) into something unintended third parties cannot decipher. The undecipherable text is referred to as ciphertext. Encryption and decryption techniques are followed when converting plaintext to ciphertext and vice versa. Three cryptographic methods are applied in the process of encrypting and decrypting data. They are asymmetric encryption, symmetric encryption, and hashing. The following section will pay closer attention to these cryptographic methods. We will also spell out the pros and cons of cryptographic methods.
1. Symmetric Cryptography
Symmetric encryption is also referred to as secret key encryption. It is a type of cryptography that only uses a single key to carry out the encryption and decryption function.
Pros of Symmetric Encryption
The following are some of the advantages of symmetric cryptography.
- It is an extremely secure type of encryption.
One of the major benefits of symmetric encryption is that it offers high levels of security for data and communication. This explains why most of the network systems belonging to the US government use this type of cryptography. The US government-designated advanced designated standard remains one of the most reliable key encryption systems.
Symmetric encryption uses the 256-bit key encryption strength. This extremely strong encryption strength would take over 10 million years for a 10 petaflop computer to figure it out using a brute force attack. In a nutshell, the 256-bit encryption strength is unbreakable.
- Relatively fast performance

Most public-key encryption systems are characterized by complexities and computational intensiveness, making them hard to operate and reducing performance. On the other hand, it is so easy to encrypt and decrypt data using symmetric keys, and this gives users great reading and writing performances by significantly reducing load times. The efficiency of symmetric encryptions is why most solid-state drives characterized by fast operating speeds tend to use them for data storage needs.
Cons of Symmetric Encryption
The following are some of the cons of symmetric encryption
- Key-sharing Limitations
The major drawback associated with symmetric encryption is the issue of key-sharing. Symmetric encryption requires the sender of the message to get the decryption key to the recipient of the data or message. This poses a crisis because encryption keys do not exist in text forms as passwords do. Instead, encryption keys are essentially blocks of meaningless and undecipherable gibberish. The sender must therefore look for a secure mode of transmitting the keys to the recipients.
- Increased scope of risk in case the key is compromised
If the symmetric key lands in the hands of malicious people, they can decrypt every information decrypted by the key and use it for malicious reasons. And because the symmetric key is used in a two-way communication line, it means that both communicating ends can become jeopardized if the key land in unsafe hands. The case is different for asymmetric encryption, wherein if the party gets hold of the key, they can only decrypt data sent your way and not that you have sent. The reason is that the data you send to other recipients will be encrypted using a different private key.
- READ MORE – 10 Cybersecurity Tips for Individuals and Students
- Smart Contracts: The Complete Details
2. Asymmetric Cryptography
Asymmetric cryptography is a dual-key encryption mechanism that uses the private and the public key to perform the encryption and the decryption functions. The public key is necessary for encrypting data, messages, or communications, whereas the private key will decrypt the said data back to plaintext. One of the widely known applications is in the operation of Secure Socket Layer (SSL) certificates. Although symmetric cryptography is also employed in SSL certificates, its drawbacks, such as slow computational times, make it a not-so-perfect choice. Asymmetric encryption had to come in to save the day.
Asymmetric cryptography will be applied when validating the browsers‘ and servers’ public and private keys when the two components meet. After that, data encryption will start by employing symmetric encryption mechanisms. This whole process is what is referred to as the SSL handshake. With data breaches skyrocketing each day, webmasters are left with no choice but to acquire SSL certificates for their websites. And one good thing is that, even with hundreds of subdomains, you can leverage the working of wildcard SSL, such as a Comodo positive wildcard SSL, to secure all the first-level subdomains under the chosen main domain.
Pros of Asymmetric Encryption
The following are some of the advantages of asymmetric cryptography
- It allows for source authentication

Because asymmetric encryption uses digital certificates, it is easy to verify the authenticity of the sources of messages. The logic here is that before a certificate authority issues a digital certificate to a requestor, it will first do its due diligence to establish the identity and legitimacy of the requestor. All the details about the requestor will be included in the digital certificate.
- Asymmetric encryption allows for non-repudiation
Like physically signed documents, an author cannot successfully dispute the validity or authorship of digitally signed data and resources.
- Asymmetric Encryption Detects Message Tampering
Asymmetric encryption puts the message recipient in great positions to detect whether or not the message was tampered with while it was in transit.
Cons of Asymmetric Encryption
The following are the drawbacks associated with asymmetric encryption
- It is Comparatively Slow
Asymmetric encryption is slow compared to symmetric cryptography. Therefore, it is not suitable for encrypting and decrypting bulky messages.
- Asymmetric encryption requires users to verify the Source of Public Keys
You must understand that with asymmetric encryption, public keys are not authenticated. As such, users will have to take the initiative of verifying that the public indeed belongs to the individuals they have specified.
- Repercussions of lost Private keys
Lost public keys often come with their fair share of dire consequences. If keys are lost, you need to reissue the certificate; otherwise, hackers can take advantage of lost keys.
Conclusion
Network security and data security are two major issues of concern in today’s internet world. Hackers have crafted sophisticated methods they use to hijack vital data and use it for the wrong reasons. Data owners have a crucial role to play in data security. They can use cryptographic methods to ensure that data is encrypted and protected from prying eyes. Asymmetric and symmetric encryption are the two most popular cryptographic methods. In your best interest, you understand how the two work and know the pros and cons of the cryptographic method. This article has provided you with all these details.
I hope this tutorial helped you to know about the What are Pros and Cons of Cryptographic Methods. If you want to say anything, let us know through the comment sections. If you like this article, please share it and follow WhatVwant on Facebook, Twitter, and YouTube for more Technical tips.
- READ MORE – 9 Things You Should Know About Cyber Security
- 4 Great Ways to Get Serious on Cybersecurity
What are the Pros and Cons of Cryptographic Methods – FAQs
What is the simple method of Cryptography?
Simple encryption algorithms, which were invited long before first computers, are based on substitution and transposition of single plaintext characters.
Which is better AES or RSA?
RSA is neither better nor worse than AES, as the two are designed for completely different use cases. RSA is an asymmetric algorithm designed for public-key cryptography. AES is a symmetric algorithm designed for private-key cryptography. It’s faster than RSA but only works when both parties share a private key.
What is encryption used for?
Encryption is the process of taking plain text, like a text message or email, and scrambling it into an unreadable format called “ciphertext”. This helps protect the confidentiality of digital data either stored on computer systems or transmitted through a network like the internet.
What is the AES 256 encryption algorithm?
The AES encryption algorithm is a symmetric block cipher algorithm with a block/chunk size of 128 bits. It converts these individual blocks using keys of 128, 192, and 256 bits.
What is RSA encryption?
RSA (Rivest-Shamir-Adleman) is an algorithm used by modern computers to encrypt and decrypt messages. It is an asymmetric cryptographic algorithm.
