Want to know about PUP? This tutorial will tell you complete details about PUP like What is PUP, how do PUPs operate, Types of PUP, how to avoid PUP, and how to remove PUP.
PUPs, or potentially unwanted programs, are referred to as such. PUAs(Potentially Unwanted Applications) are software programs that you probably didn’t want to be installed on your computer. They are also known as bundleware, junkware, or PUAs.
Introduction

PUPs are a class of software that, though they may not always be malicious, can harm your computer or device in several ways. Users may unintentionally install PUPs without realizing their possible consequences because they frequently come packed with legitimate software. The goal of this paper is to give a thorough overview of PUPs, including risks, safeguards, and efficient eradication techniques.
PUPs, or potentially unwanted programs, are a rising problem for internet users everywhere. They frequently come bundled with trustworthy software and can set themselves up without the user’s knowledge or permission. Once installed, they can slow down your computer, show intrusive pop-up adverts, and potentially steal your personal information, among other issues. But what precisely are PUPs, and how can you safeguard against them? We shall define PUPs, describe how they operate, and discuss how to avoid them in this post. You will have the information and resources needed to keep your computer clear of possibly malicious programs by the time you finish reading this article.
What is PUP

A potentially Unwanted Programme is referred to as PUP. It refers to computer or device software that may not be specifically malicious but has the potential to cause several problems. PUPs frequently infiltrate a system via software bundling, deceptive advertising, or drive-by downloads, when consumers accidentally install them without understanding the potential repercussions.
The acronym PUP stands for Potentially Unwanted Programme in the context of cybersecurity. These programs, as their name suggests, could potentially damage your computer but their presence is undesirable. PUPs come in a variety of shapes and sizes, including, but not limited to, adware, spyware, browser hijackers, and toolbars.
PUPs normally have valid functionality but may display unpleasant behavior or pose threats to privacy and security. In contrast to malware, which is purposefully designed to harm a system or steal data, PUPs may do these things. Adware, browser hijackers, toolbars, and system optimizers are a few PUP examples.
- Related: What Is A Streaming Stick? 5 Best Streaming Sticks
- What Is A Virtual Machine? 5 Best Virtual Machine Software
How do PUPs operate?
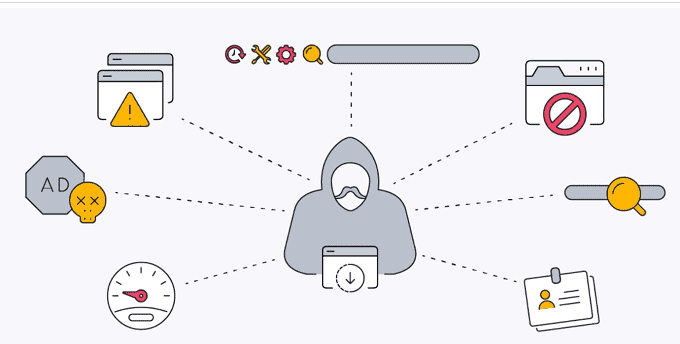
Potentially Unwanted Programs (PUPs) can exhibit various behaviors and have different functionalities, but they generally have the following characteristics:
- Unwanted Advertising: Many PUPs are designed to display excessive and intrusive advertisements. They may inject ads into websites you visit, show pop-up windows, or generate in-text ads within the browser. These ads can be disruptive, and annoying, and negatively impact your browsing experience.
- Browser Modifications: Certain PUPs modify browser settings without your consent. They may change your default search engine, homepage, or new tab page to redirect your web traffic to specific websites or search engines. These modifications can be difficult to reverse and may interfere with your ability to use your preferred browser settings.
- Data Collection: Some PUPs collect user data, including browsing habits, search queries, IP addresses, and other personally identifiable information. This data is often used for targeted advertising or may be sold to third-party companies for marketing purposes. PUPs can compromise your privacy and expose you to potential identity theft risks.
- System Performance Impact: PUPs can consume system resources, leading to decreased performance and slower computer speeds. They may run unnecessary processes in the background, use up memory or CPU power, and cause system crashes or freezes.
- Unauthorized Software Installations: PUPs often sneak into your system bundled with legitimate software downloads. They install themselves without your explicit consent or by using deceptive techniques. PUPs can create additional files, registry entries, and startup processes, making them challenging to remove completely.
- Browser Hijacking: Some PUPs take control of your browser, redirecting your searches to unfamiliar or unwanted websites. They may prevent you from accessing certain legitimate websites or force you to visit specific websites that they promote. This can be frustrating and hinder your ability to use the internet effectively.
- Fake Security Warnings: Certain PUPs masquerade as security software or system optimizers. They display fake alerts or warnings about supposed threats or system issues on your computer. These scare tactics aim to convince you to purchase their full version or provide sensitive information, preying on your fear of malware or system vulnerabilities.
- Unwanted Toolbars and Extensions: PUPs may install additional toolbars or browser extensions without your consent. These toolbars often clutter your browser interface, affect its functionality, and may include unwanted features like ad injection or data tracking.
It’s important to note that while PUPs may not be inherently malicious, they can still negatively impact your computer’s performance, compromise your privacy, and diminish your online experience. Removing PUPs is crucial to maintaining a clean and secure system.
- Related: What is Vimeo Used for? Review & Features You Must Know
- What Is a RAR File? Details about RAR format, Archiever, and Extractor
Types of PUP
Potentially Unwanted Programs (PUPs) encompass various types of software that may exhibit unwanted behavior or pose risks to the user’s system. Here are some common types of PUPs:
- Adware: Adware programs display unwanted advertisements, often in the form of pop-ups, banners, or in-text ads. These ads may be intrusive, and disruptive, and can slow down the system. Adware is typically bundled with free software and is designed to generate revenue for the developers by displaying targeted ads to users.
- Browser Hijackers: Browser hijackers modify browser settings without the user’s consent, such as the default search engine, homepage, or new tab page. They often redirect web traffic to unwanted websites or display altered search results that contain sponsored links. Browser hijackers can degrade the browsing experience, expose users to potentially malicious websites, and collect browsing data for targeted advertising purposes.
- Toolbars and Extensions: Some toolbars and browser extensions, although not inherently malicious, can be classified as PUPs. These add-ons often come bundled with software downloads and can modify browser settings, display ads, track user activity, or collect personal information.
- System Optimizers: Certain system optimizers claim to improve system performance by cleaning up junk files, optimizing settings, or fixing registry issues. However, many of these programs exaggerate or fabricate system problems to convince users to purchase the full version. Some system optimizers may also include additional unwanted features or bundle other PUPs.
- Spyware: While spyware is typically considered a more malicious form of software, some less intrusive spyware programs may fall into the PUP category. These programs collect user data without explicit consent, such as browsing habits, keystrokes, or personal information, often for marketing purposes.
- Fake Security Software: Also known as scareware, fake security software masquerades as legitimate antivirus or anti-malware programs. These PUPs often display alarming messages about non-existent threats and prompt users to purchase the full version to remove them. Fake security software can deceive users into providing sensitive information or paying for unnecessary and ineffective services.
Above are some of the types of PUP. It’s important to note that the classification of a program as a PUP may vary depending on different antivirus or security software vendors.
- Related: What is GoToMeeting? World’s Top, Easy-To-Use, And Secure Web Conferencing Tool For Businesses
- What Is Intel Proset Wireless Software?
How to avoid PUP

To avoid Potentially Unwanted Programs (PUPs) and minimize the risk of their installation on your computer or device, here are some preventive measures you can take:
- Download Software from Trusted Sources: Obtain software only from reputable and official sources. Avoid downloading applications from unfamiliar websites or third-party sources, as they are more likely to bundle their software with PUPs.
- Read End User License Agreements (EULAs): Take the time to read the terms and conditions of EULAs before installing any software. Pay attention to any clauses that mention additional software or changes to your system settings. If you encounter any suspicious or unclear statements, consider aborting the installation.
- Customize Installation Options: During the software installation process, choose the “Custom” or “Advanced” installation option rather than the “Express” or “Quick” installation. This allows you to review and control what additional components or software are being installed. Be vigilant and deselect any optional software or features that you don’t need or recognize.
- Be Wary of Deceptive Advertising: Exercise caution when clicking on ads or links, especially those that claim to offer free software, system optimizations, or security scans. These ads can lead to websites that distribute PUPs or trick you into downloading unwanted programs. Avoid engaging with deceptive or suspicious advertisements.
- Keep Your Software Updated: Regularly update your operating system, web browsers, and other software to ensure you have the latest security patches and bug fixes. Software updates often include security enhancements that can help protect against PUPs and other threats.
- Be Cautious with Freeware and Shareware: Free software and shareware often come bundled with additional programs. Pay attention to the installation process and follow the steps mentioned earlier to customize the installation and avoid installing unwanted software.
- Use Reputable Security Software: Install a reputable antivirus or antimalware program and keep it up to date. Security software can detect and block PUPs during the installation process and provide real-time protection against various threats, including PUPs.
- Disable or Limit Browser Extensions: Review the extensions installed in your web browser and disable or remove any that you don’t use or trust. Some extensions may be associated with PUPs or exhibit unwanted behavior.
- Exercise Caution Online: Be cautious when downloading files or clicking on links from unfamiliar or suspicious websites. Stick to reputable websites and exercise good browsing practices, such as avoiding clicking on unsolicited pop-ups or suspicious download links.
By following these preventive measures, you can significantly reduce the likelihood of PUP infections and maintain a more secure and hassle-free computing experience.
- Related: What is 1Password, 1Password Features, Price & Review
- What is Revit, What is Revit used for, Revit Review
How to Remove PUP

To remove Potentially Unwanted Programs (PUPs) from your computer or device, you can follow these general steps:
- Uninstall from Control Panel (Windows): Open the Control Panel on a Windows computer, then choose the Programmes section. A list of all installed programs will now appear. Click the Uninstall button in the top bar after choosing the program you want to remove. To completely delete the software from your computer, adhere to the removal instructions. For Mac: Open the “Applications” folder, locate the PUP or associated program, and drag it to the Trash. Then, right-click on the Trash and select “Empty Trash” to completely remove the program.
- Uninstall from Applications (Mac): The uninstall procedure varies somewhat for Apple PCs. Open the Finder and choose the name of your MacBook or Mac from the left-hand menu bar to uninstall any software that was not downloaded from the Mac App Store. The internal hard drive of the computer must then be opened. This is identified as Macintosh HD by default. All installed programs can be found in the Applications subdirectory. Simply drag and drop the desired program into the Dock’s trash can to finish. This will completely remove the desired software. Click the trash can with two fingers, then choose “Empty Trash” to free up the storage space.
- Scan with Antivirus or Antimalware Software: Antimalware protection tools can scan a device and eliminate the application to automatically find and remove PUPs. Applications like Malwarebytes or Zemana AntiMalware are examples of antimalware programs that are capable of detecting and eradicating PUPs.
- Check Startup Programs: To stop downloading PUPs in the future, always check the terms and conditions before downloading any software on your computer because some PUPs could be packed with trustworthy programs. In addition, free software downloads from the internet should be used with caution as PUPs are frequently spread this way.
- Utilize PUP Removal Tools: Some security software providers offer specialized tools or dedicated PUP removal tools. These tools are designed specifically to detect and remove PUPs. Check if your antivirus software provides such tools and use them accordingly.
It’s important to note that manual removal methods may vary depending on the specific PUP and the operating system you’re using. If you’re unsure or uncomfortable with manual removal, consider seeking assistance from a professional or using reputable cleanup tools recommended by your antivirus software like AVG ultimate or Intego Mac premium bundle.
Conclusion
Our blog entry on potentially unwanted programs (PUPs) is intended to provide you with a better understanding of what they are and how to safeguard your computer from them. PUPs can be annoying and even harmful, but you can avoid them if you have the appropriate information. To stop PUPs from harming your computer, be sure to frequently scan it with antivirus software and keep it updated. Don’t forget to pass along this knowledge to your loved ones so they can be secure online as well!
I hope this tutorial helped you to know about the “What is PUP“. If you want to say anything, let us know through the comment sections. If you like this article, please share it and follow WhatVwant on Facebook, Twitter, and YouTube for more Technical tips.
- Related: What is Ethical Machine Learning? Ensuring Fairness, Transparency, and Responsibility in the Age of AI
- What Is Application Security and Why Is It Important?
What is pup – FAQs
What does a PUP look like?
Despite the user’s consent to download it, a program that may be unwelcome is known as a potentially unwanted program, or PUP. Spyware, adware, or extra web browser toolbars are a few examples of PUPs. These programs are frequently downloaded along with ones that the consumer genuinely needs.
How do PUP domains work?
Based on the malware-discoverer, a blocklist of domains that house potentially unwanted programs (PUP). Every day, Blocklist is updated twice. There are several forms available; depending on the program used, refer to the relevant section: URL-based portion of uBlock Origin (uBO) (recommended)
What exactly is a computer PUP?
PUPs, or potentially unwanted programs, are referred to as such. PUAs (Potentially Unwanted Applications) are software programs that you probably didn’t want to be installed on your computer. They are also known as bundleware, junkware, or PUAs.
What purposes does PUP serve?
PUPs have the ability to alter system settings, show unwanted adverts, install other unwanted software, and adjust web browser settings.
